More than 33% of discovered vulnerabilities across the full stack are rated critical or high severity, underscoring how quickly small visibility gaps can escalate into serious exposure.
The increase points to a broader industry challenge: organizations are detecting issues faster, yet still struggling to understand which weaknesses truly matter and how attackers might exploit them.
This blog breaks down the imperative of vulnerability assessments and penetration testing—two complementary methods for identifying and validating security weaknesses.
It includes:
- How do pen tests vs vulnerability assessments work
- Benefits and challenges associated with penetration test vs vulnerability assessment
- How FlowAssure streamlines penetration testing for enhancing security oversight
Key Takeaways
- Vulnerability assessments reveal broad security weaknesses, while penetration testing validates how those weaknesses can be exploited in real attack scenarios.
- Using both methods together provides stronger risk accuracy, faster remediation, and clearer prioritization across complex environments.
- Many challenges—like incomplete vendor visibility, inconsistent evidence, and point-in-time pen test results—stem from fragmented processes rather than tooling alone.
- FlowAssure’s AI agents streamline questionnaires, compliance reviews, and pen test analysis, giving security teams consistent, scalable governance without increasing headcount.
|
Penetration Testing vs Vulnerability Assessment: What Are The Differences?
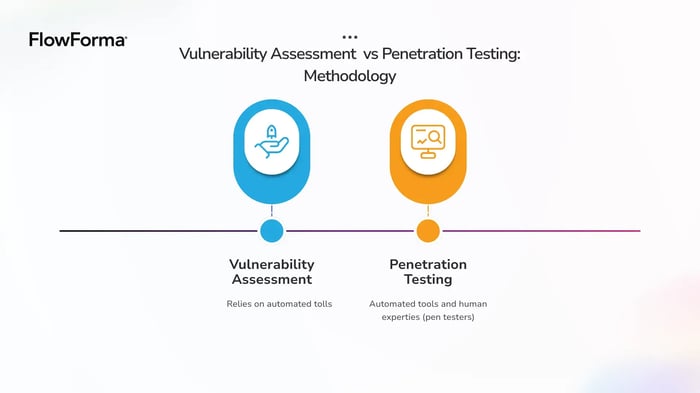
Vulnerability assessment vs penetration test
Below is a comparison of pen test vs vulnerability assessment, capturing the key differences security leaders consider when evaluating system security.
|
Category
|
Vulnerability Assessment
|
Penetration Test
|
|
Ideal for
|
Routine vulnerability management
|
Validating controls through real attack scenarios
|
|
Primary purpose
|
Identify known vulnerabilities and misconfigurations across systems
|
Simulates real-world attacks to exploit vulnerabilities and reveal security flaws
|
|
Depth of analysis
|
Broad, automated visibility
|
Manual in-depth analysis and penetration testing
|
|
Tools used
|
Vulnerability scanning tools
|
Penetration testing tools + skilled testers
|
|
Output
|
A detailed report of findings
|
Evidence of real-world impact and exploitation paths
|
|
Frequency
|
Regular vulnerability scans
|
Periodic or event-based engagements
|
|
Who executes it
|
Internal teams or MSSPs
|
Ethical hackers and penetration testers
|
An overview of pen testing vs vulnerability scanning
The following sections build on this foundation to explain the differences between vulnerability assessment and penetration testing.
What Is Vulnerability Scanning?
Vulnerability scanning is a core component of a security assessment, designed to identify known, detectable issues—such as misconfigurations, missing patches, exposed services, and other potential weaknesses—across on-premises and cloud environments, rather than uncovering zero-day threats or complex logic flaws.
Vulnerability scanning at a glance
It provides a structured way to evaluate system security by checking assets for outdated software, missing patches, and known exposure points that attackers may attempt to exploit.
Vulnerability scanning supports the assessment process by detecting known, observable weaknesses across systems and environments. The broader vulnerability assessment then contextualizes these findings—evaluating risk, potential impact, and exposure—so security teams can prioritize remediation before threat actors exploit the same gaps.
How does automated vulnerability scanning work?
.webp?width=700&height=467&name=Infographic%20illustrating%20how%20vulnerability%20scanning%20works%20(1).webp)
The process of vulnerability scanning
Automated vulnerability scanning tools evaluate systems, applications, and network components using signatures, CVE databases, and configuration policies to identify vulnerabilities that may introduce security risks.
These automated tools highlight weak configurations, missing patches, and known security weaknesses, then provide severity scores to support a structured risk assessment.
A typical vulnerability testing cycle includes:
- Discovering assets and identifying services, devices, and open ports
- Scanning for known vulnerabilities and misconfigurations
- Assigning severity scores and generating remediation guidance, which often requires human review and validation before action
- Running on a schedule to support continuous monitoring across environments
The 7 Core Benefits of Vulnerability Scanning
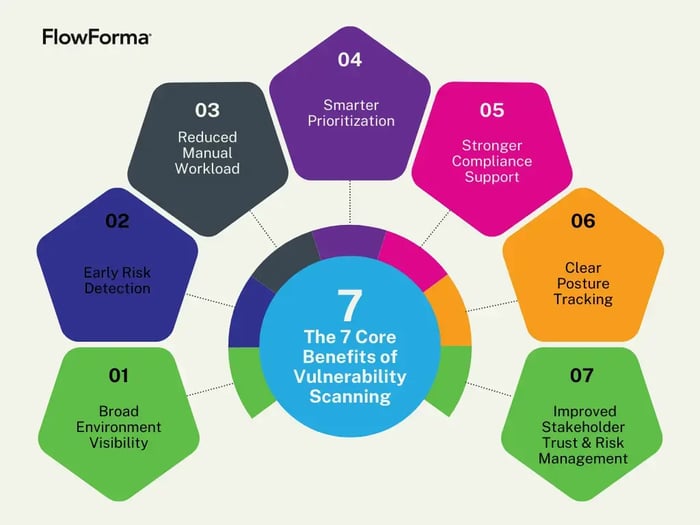
7 benefits of vulnerability scanning for tightening IT security
Done consistently, vulnerability scanning provides a structured way to reduce risk and maintain stronger visibility across systems and vendors. The following are its major benefits for an organization's security posture:

An introduction to FlowAssure
-
Provides broad visibility across complex environments by identifying unmanaged cloud instances, exposed services and ports, outdated third-party components, and other known security gaps across cloud assets and endpoints. Tools like FlowAssure strengthen this insight by correlating scan results with validated vendor documentation downstream, adding context without implying that scanners themselves perform vendor validation.
-
Enables early detection of high-risk issues, identifying new Common Vulnerabilities and Exposures (CVEs), weak configurations, and missing patches soon after disclosure to reduce the likelihood of initial access or exploitation.
-
Reduces manual workload by automating the identification and ranking of vulnerabilities.
-
Improves prioritization and remediation planning by applying models such as the Common Vulnerability Scoring System (CVSS) and Exploit Prediction Scoring System (EPSS). As a result, teams can decide which issues require immediate patching and which can be scheduled for later remediation based on real-world exploit likelihood.
-
Strengthens compliance documentation, generating recurring evidence needed for Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), and other audits.
-
Enhances visibility into changes in security posture, showing how risk levels evolve across scheduled scans.
-
With a 34% increase in attackers exploiting vulnerabilities to gain initial access and cause security breaches, routine vulnerability assessments demonstrate responsible risk management and signal that the organization maintains a reliable security program.
Key Challenges of Vulnerability Scanning in 2026
Even with strong automation, vulnerability scanning has practical limitations—especially when applied across distributed systems and diverse vendor ecosystems.
1. Incomplete or inaccurate asset information
Scanners depend on accurate inventories. Missing or outdated vendor details weaken scan results and create blind spots. Tools like FlowAssure help surface these gaps by reviewing vendor documentation for completeness.
FlowAssure Product Showcase
2. High scan volume and prioritization issues
Large enterprises generate thousands of findings, making it difficult to pinpoint which vulnerabilities matter most. When vendor inventories are incomplete or security questionnaires lack detail, scan results provide a fractured picture of actual risk.
Quinn, FlowAssure’s questionnaire agent, supports prioritization by flagging inconsistencies in vendor questionnaire responses and surfacing areas that require closer review. 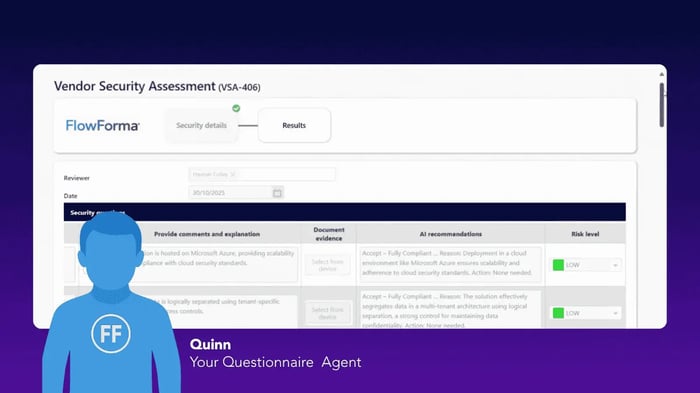
Quinn assisting with security questionnaires
Quinn automates security questionnaire analysis—flagging inconsistencies, missing information, and incomplete responses before they create blind spots in your risk assessment.
3. Limited insight into real-world exploitation paths
Scanners detect flaws but can’t determine how attackers may chain them together across systems or vendors. By consolidating vendor evidence, FlowAssure helps teams understand where deeper analysis or penetration testing may be necessary.
4. Coordination challenges during remediation
Fixing vulnerabilities across hybrid environments and vendor networks requires coordination between multiple internal teams and external parties. Compounding this, organizations must also validate vendor compliance through ISO 27001 certificates and SOC 2 Type II reports.
FlowAssure's dedicated AI agents, Iris and Sam, automatically review these compliance documents respectively, validate controls, and detect documentation gaps. Meanwhile, the platform tracks remediation timelines, escalates overdue vendor commitments, and maintains complete audit trails.
5. Compliance demands with limited staffing
Continuous assessments and regular evidence collection can strain lean security teams. FlowAssure lightens the load by validating vendor documents and organizing assessment evidence centrally, making compliance easier to maintain.

FlowAssure’s compliance module
What Is a Penetration Test?

What is pen testing?
A penetration test moves beyond automated scanning by evaluating whether attackers could actually exploit vulnerabilities under realistic conditions. It focuses on breach outcomes by simulating real-world attacks, revealing how far an attacker can progress and what assets are at risk, beyond what routine vulnerability testing can show.
During a pentest, skilled penetration testers attempt to uncover potential weaknesses, chain vulnerabilities across systems, and assess how deeply an attacker could move inside critical systems.
The Top 5 Penetration Test Benefits
Penetration testing builds on vulnerability scanning by showing how far an attacker could advance in a real compromise. Instead of listing weaknesses, it demonstrates the actual impact of exploitation, helping security teams understand which issues pose meaningful business risk.
Key benefits include:
1. Clearer understanding of real business risk
A penetration test demonstrates whether attackers can bypass controls, move through critical systems, or manipulate sensitive processes within a defined scope and timeframe. It allows leadership to distinguish theoretical vulnerabilities from issues that could disrupt operations or expose sensitive data.
2. Identification of chained attack paths
Pentesters reveal how multiple weaknesses combine across applications, networks, and integrations. These multi-step attack paths—including privilege escalation, lateral movement, and exploitation sequences—are often invisible to scanners and provide insight into how complex attacks unfold in practice.
3. Insight into incident readiness and response gaps
Simulated intrusions test how effectively teams detect, escalate, and contain malicious activity. Pentest results frequently expose delayed alerts, unclear ownership, or gaps in monitoring that would hinder a real investigation.
4. Stronger evidence for compliance and assurance
Regulatory frameworks require periodic penetration testing to validate the effectiveness of security controls. Pentest reports serve as documented proof of due diligence during internal audits and vendor assessments.
5. Validation of vendor-claimed security controls
Penetration testing simulates real-world attacks within an agreed scope to reveal whether a vendor’s stated controls, such as authentication, authorization, encryption, logging, or network segmentation, function as intended. Gaps between documented policies and operational reality become immediately apparent.
5 Challenges of Penetration Testing (& How FlowAssure’s AI Agent Solves Them)
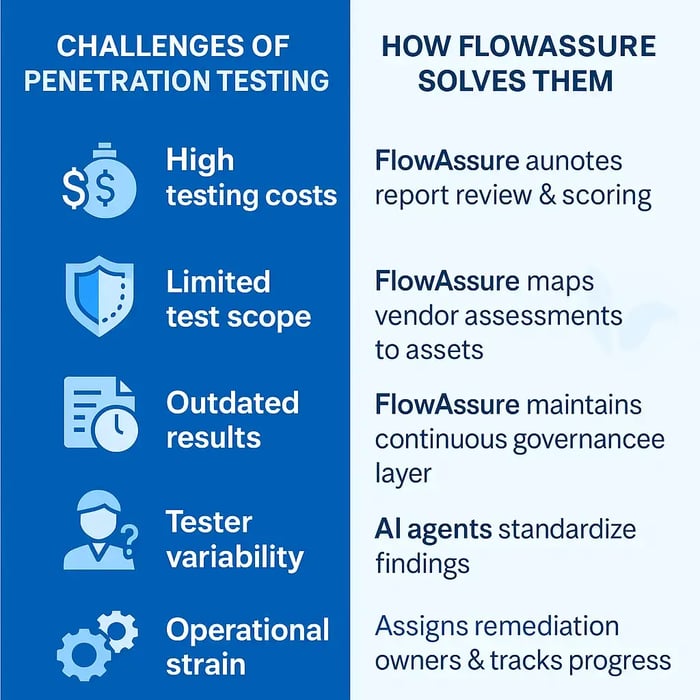
Challenges associated with pen testing + how FlowAssure solves them
While penetration testing provides valuable insight into how attackers could exploit vulnerabilities, several constraints can limit its effectiveness—especially in large vendor ecosystems. FlowAssure’s pen test agent, Penn, helps organizations handle these challenges more efficiently.
1. High testing costs and limited expertise
Penetration testing requires specialized skill and is expensive to conduct at scale. Complex tests targeting critical systems can exceed US $50,000, and time-boxed engagements limit how deeply testers can explore potential weaknesses.
How FlowAssure helps:
Penn automates the review of vendor-submitted penetration test reports, extracting vulnerabilities, CVSS scores, impacted assets, and exploit paths.

Pen test findings overview
By classifying findings based on severity and business context, Penn eliminates days of manual analysis and allows security teams to evaluate more vendors with consistent rigour.
2. Limited test scope and inconsistent coverage
Pentests occur periodically and may not cover every target system, especially in multi-cloud or vendor-managed environments, leaving some potential entry points untested and creating uneven visibility across the attack surface.
How FlowAssure helps:
FlowAssure consolidates all vendor assessments and maps them to relevant assets, helping teams identify untested areas. Penn also detects recurring issues across multiple vendor reports, revealing patterns that may indicate deeper systemic risks.
3. Snapshot results in fast-changing threat conditions
Penetration testing reflects conditions at a single moment. As attackers develop new methods to exploit vulnerabilities, earlier results lose relevance and can give organizations a false sense of security.
How FlowAssure helps:
Penn monitors high-risk findings and flags indications of evolving threats.
FlowAssure triggers follow-up risk workflows when results age out or when changes in vendor posture require updated testing—helping teams maintain an accurate, current view of overall security posture.
4. Tester variability and inconsistent reporting
Penetration testing outcomes depend on a tester’s methodology and communication style. Some reports capture detailed exploitation paths, while others lack context or omit subtle software vulnerabilities, complicating remediation.
How FlowAssure helps:
Penn standardizes evaluation across all vendor reports, converting raw pentest data, regardless of format, into structured insights with clear remediation recommendations.
The process reduces interpretation errors and ensures results consistently meet internal expectations.
5. Operational strain during remediation
Addressing pentest findings requires cross-team coordination, vendor responses, and continuous tracking. Without centralized oversight, vulnerabilities found may remain unresolved due to unclear ownership or communication gaps.
How FlowAssure helps:
FlowAssure assigns remediation owners, tracks timelines, escalates overdue tasks, and maintains complete audit trails. By integrating Penn’s scoring with workflow automation, the platform ensures that identified vulnerabilities translate into actionable, well-managed remediation work.
What Security Policies Do I Need For Tightening IT Governance?
A strong vulnerability assessment and penetration testing strategy relies on well-defined governance policies. These policies clarify responsibilities, testing requirements, evidence expectations, and the conditions under which assessments must be performed.
While some policies support both testing methods, others align more closely with the hands-on nature of penetration testing.
|
Policy Type
|
For Vulnerability Scanning
|
For Penetration Testing
|
|
Vulnerability Management Policy
|
Establishes how often scans run, how findings are documented, and how remediation targets are set.
|
Supports retesting and verification after pentest findings are addressed.
|
|
Penetration Testing Policy
|
Not always required unless scans trigger targeted tests.
|
Defines objectives, testing techniques, data handling rules, boundaries, and vendor coordination.
|
|
Change Management Policy
|
Ensures new assets and updates are added to the scanning scope.
|
Specifies when pentests must occur after major system or application changes.
|
|
Incident Response Policy
|
Guides teams when high-severity vulnerabilities are detected.
|
Helps structure communication and investigation when pentesters identify exploitable attack paths.
|
|
Vendor Security Policy
|
Required when third-party scanning services or cloud assets are in scope.
|
Ensures external testers follow required controls and reporting standards.
|
|
Compliance and Audit Policy
|
Outlines how scan data and documentation are stored for audits.
|
Defines how pentest evidence, approvals, and remediation steps are retained.
|
|
Asset Inventory/ITAM Policy
|
Ensures all assets—including vendor-managed ones—are included in scanning.
|
Helps scope pentests accurately and prevents omission of critical systems.
|
|
Data Classification Policy
|
Supports risk scoring by indicating the sensitivity of affected data.
|
Critical for defining what testers may access or simulate during exploitation attempts.
|
Security Policies for Vulnerability Scanning vs Penetration Testing
5 Ways FlowAssure Streamlines Penetration Test Management
Managing penetration testing across multiple vendors often requires reconciling different report formats, evidence types, and testing methodologies. FlowAssure simplifies this by providing a structured environment that standardizes how pentest outcomes are interpreted, documented, and incorporated into broader vendor risk decisions.
1. Standardized interpretation of diverse report formats
FlowAssure applies consistent logic to extract key details, ensuring every report—regardless of structure—feeds into a unified evaluation workflow.
2. Clear linkage between findings and vendor-supplied evidence
FlowAssure connects pentest findings with supporting documentation such as security questionnaires, ISO 27001 certificates, and SOC 2 Type II reports.
Teams can then confirm whether identified weaknesses align with the vendor’s stated controls.
3. Improved decision-making for vendor approvals
Instead of relying solely on subjective reviewer judgment, FlowAssure integrates pentest results into broader vendor risk scoring models, making approval decisions more consistent across the organization.
4. Full traceability across remediation requirements
FlowAssure ties pentest findings to required actions, relevant vendor commitments, and compliance expectations, giving teams a structured view of impact and readiness.
5. Scalable governance as vendor portfolios grow
FlowAssure provides a standardized framework for how pentest results are handled, reviewed, and incorporated into risk models—keeping governance stable as the portfolio expands.
Automate Vendor Pen Test Analysis With FlowAssure, Without Compromising Accuracy
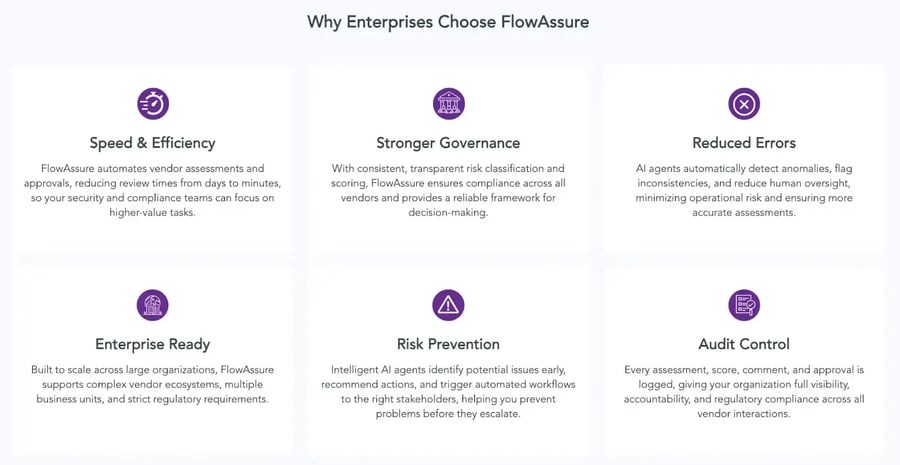
Key features of FlowAssure
Vendor penetration test reports vary widely in format and depth, making cross-vendor comparisons difficult. Whether you’re reviewing a new vendor’s pentest or monitoring ongoing risk across your supply chain, FlowAssure centralizes evidence, improves consistency, and supports smarter vendor governance.
Book a personalized demo to see how FlowAssure can simplify penetration testing governance and audit readiness.
FAQs
1. How do I decide the right frequency for penetration testing?
Pen test frequency depends on system sensitivity, regulatory requirements, and how often your environment changes. High-impact systems or those exposed to external users typically require more frequent testing than internal applications with stable architectures.
2. What should I request from vendors beyond a standard pen test report?
Ask vendors for supporting evidence such as remediation verification, retest results, exploit proofs-of-concept, and updated controls documentation. These help validate whether identified vulnerabilities were resolved and whether the findings align with your organization’s risk thresholds.
3. How do vulnerability assessments support board-level risk reporting?
Vulnerability assessments quantify exposure across assets, severity categories, and business units, giving leadership a clearer view of systemic risk. Trend data helps boards evaluate whether security posture is improving and whether resource allocation aligns with identified risk areas.
4. How does FlowAssure help validate the quality of vendor-provided pen test reports?
FlowAssure’s Penn agent reviews reports for completeness, checks severity scoring consistency, and highlights unclear or unsupported findings. Teams can then spot weak testing methodologies or gaps in vendor assessments that might otherwise go unnoticed.
5. Can Penn detect patterns or recurring issues across multiple vendor pen tests?
Penn correlates findings across all vendor assessments to reveal recurring weaknesses, aging vulnerabilities, or systemic control failures. Security teams gain higher-level insight into ecosystem-wide risks, rather than focusing solely on individual vendor issues.
.png)



.webp?width=700&height=467&name=Infographic%20illustrating%20how%20vulnerability%20scanning%20works%20(1).webp)











